| Protocol | Protocol Number |
| EIGRP | 88 |
| OSPF | 89 |
Wednesday, December 28, 2011
Difference between Protocol number and Port number
Monday, December 26, 2011
Different types of communication systems
Simplex
In this type of communication, first device send data and second device receive it. Second device never send any information to first device. Broadcast systems like FM radio work in this way.
Half Duplex
In this type of communication, when first device send data, second device receives it and when second devices send data, first device receives it. But both devices can’t send or receive data at the same time. This type of communication is using in "walkie-talkie".
Full Duplex
In this type of communication, first and second device can send and receive data simultaneously. Phones and mobile phones are using this type of communication.
Note: In Ethernet communication we can set both end half or full duplex depending up on the requirements. That is Ethernet can work on both mode.
Sunday, December 25, 2011
Basic Switch Configuration
Before begin configuration we need to see the current status of switch. This can be don using verity of ‘show’ commands. Some of them are given below
- SW1#Show int status ;shows description of ports, status, VLAN in which port is connected to, duplex, speed of each interface etc.
- SW1#show int fa0/1 ;This command shows interface specific details like Transmission rate, error state, etc.
- SW1#show run int fa0/1 ;This command shows the commands entered under the interface fa0/1, in the running configuration
- SW1#show power inline : This command shows the power settings of each port. Used for VoIP devices. If you don’t know about inline power, please check here
Now, lets set the interface attributes
Setting interface attributes
The syntax is as follows:
interface type mod/port
speed {10 | 100 | 1000 | auto} ;This command tells transmission speed. It can be set depending on Speed of Interface. Normally Switch detects the speed correctly. Default configuration is “auto” ie. automatically detect the speed
duplex {half | full | auto} ;set the duplex of interface. Default is auto. But it is better to hardcode by command on both side. If you set duplex to auto then make it on both side. Also, if you set duplex make sure that it is typed on both side, otherwise mismatch will happen. If you don’t know about duplex, please check here
mdix auto ;This is the default setting. . This permit switch to automatically discover if a crossover connection is needed. we can change the setting by “no mdix auto” command
media-type {sfp | rj45} ;detects automatically. sfp used for fiber optic ports
Sample configuration is given below:
SW1(config)#interface fa0/1
SW1(config-if)#speed 100
SW1(config-if)#duplex full
SW1(config-if)#no shut (to enable the interface)
Ok. That’s enough. But the problem is, we have to type it on all interface. Hmm… It has an easy way – use the ‘range’ command
SW1(config)#int range fa 0/1 - 4 , fa0/15 ;comma is surrounded by space. This will select the specified range of interfaces i.e. from fa0/1 to fa0/4 and fa0/15 at the same time. Now we can set any attributes to that interface.
SW1(config-if-range)#shut
Setting inline power
SW(config-if)#power inline {auto|never} :to automatically discover power need by port or disable power
SW(config-if)#power inline {consumption mw | static max mw} : to give power specifically
Saturday, December 24, 2011
Inline Power / Power over Ethernet (PoE)
Inline Power and PoE are used to provide power to IP phones, wireless access points etc. by the catalyst switch trough the same data cable.
In the reality, as you may know, out of 8 channels in the UTP cable, only 4 is used for data transmission. So these methods use the rest to provide power to the devices. 
Cisco Provides 3 methods to deliver current through the Ethernet cable:
- Cisco Inline Power
- 802.3af PoE
- 802.3at PoE+
| Property | Inline Power | 802.3af | 802.3at PoE+ |
| Standard | Cisco Proprietary | IEEE standard | IEEE standard |
| Maximum power delivery | 7W/port | 15.4W/port | 34.20 W |
| Cable speed | 10/100 only | Compatible with gigabit Ethernet | Compatible with gigabit Ethernet |
| Compatibility | Incompatible with all non-Cisco devices that accept power over Ethernet | Not compatible with Cisco inline power – the power negotiation process is completely different | Backward compatible with 802.3af |
The devices connecting to the port are divided into different classes depending up on the power consumption:
| Class | Max Power | |
| 0 | 15.4 W | Default |
| 1 | 4.0 W | |
| 2 | 7.0 W | |
| 3 | 15.4 W | |
| 4 | Undefined | Future Use |
Some advantages of using these methods are:
- Centralized point of power
- Centralized point of backup
- Cheaper cabling
Configuration
Switch#show power inline ;to see the current status of ports
Switch(config-if)#power inline {auto|never|delay}
- auto: automatically detect power
- never: to disable power supply through that port
- delay: wait up to the given delay time before turning off the power of that port if the phone went offline. This is useful when phone is rebooting.
Switch(config-if)#power inline {consumption mw | static max mw} ;to give power specifically
Note: We don’t need to type any command. Cisco switch detect all cisco devices and power needed by the devices automatically using CDP.
Friday, December 23, 2011
VTP
VTP stands for VLAN Trunking Protocol. Unlike the name implies, VTP is used for replication of VLAN information. That means, we just need to create VLANs or edit VLAN information only on one switch. Then VTP will transfer that information through the trunk link to all other switches which make the administration centralized.
VTP works based on the revision number. By default, VTP revision number is 0 on all switches. If we change any VLAN information on a switch, like… adding VLAN, deleting VLAN, renaming VLAN, etc.. the revision number increases. When other switches get the VTP update, it check the VTP revision number contained in the update with its on VTP revision number. If the local revision number is lower than the one it received, it replace the whole VLAN database with the currently received database.
VTP has three modes – Server, Client and Transparent. Depending upon VTP mode in which the switch operates, it gets the features as follows:
- Server(default)
- Power to change VLAN information
- Sends and receives VTP updates
- Saves VLAN configuration
- Client
- Cannot change VLAN information
- Sends and receives VTP updates
- Does not save VLAN configuration
- Transparent
- Forwards(passes through) VTP updates
- Does not listen to VTP advertisements i.e.. it does not update its VLAN information using the VTP updates from other switches
- Power to change local VLAN information
- Saves VTP configuration (local)
By default cisco switches comes with VTP server mode. Because of there is no VTP Domain name applied to new switches, they act as server for themselves. Also, switches doesn’t participate in VTP until they hear VTP advertisement from another switch.
To see the current VTP status, use the following command
Now lets make VTP run on every switch as in the figure.
Set VTP management domain name on all switches
SW1# vtp domain TestDomain
SW2# vtp domain TestDomain
SW3# vtp domain TestDomain
Note: If there is no domain name exist in all switches, then if we configure domain name on SW1, all switches get it automatically.
Set VTP mode of each switch
SW1# vtp mode server
SW2# vtp mdoe transparent
SW3# vtp mode client
Set VTP password (optional)
eg: SW1# vtp password P1ssw0rd
Note: if we want to set the password, set it on all switches
Set VTP version
Default VTP version is 1. if we want to change it to version 2, then do the following command on all switches
eg: SW1# vtp version 2
VTP synchronization issues
If we accidently connect a switch with higher revision number and same domain name to the network, all the switches will replace their database to it’s database. Then network connection may not available to users.
Solution:
Before attaching the switch to the network, reset its revision number to zero. Do one of the following to reset revision number to 0
- Change VTP mode to transparent, then back to server
- Change VTP domain to a bogus name, then back
Thursday, December 22, 2011
Private VLAN
Private VLAN is the technique of dividing single VLAN into different sub VLANs. This is generally used in the ADSL networks. Also, we can use it to simplify the IP address assignment because all ports are in the same subnet, although they are logically separated in the data link layer.
Private VLAN contains two components
- Primary VLAN, which is the real VLAN
- Secondary VLANs, which are the sub VLANs
Secondary VLANs can be one of these:
- Isolated
- Ports associated with this VLAN cannot communicate each other
- Ports associated with this VLAN cannot communicate with any other private VLAN
- Ports associated with this VLAN can communicate only with Primary VLAN
- Community
- Ports associated with this VLAN can communicate each other
- Ports associated with this VLAN cannot communicate with any other private VLAN
- Ports associated with this VLAN can communicate only with Primary VLAN
Now lets, Create these VLANs as in the figure
Creating Community VLANs
Sw1(config)# vlan 100
Sw1(config-vlan)#private-vlan community
Sw1(config)# vlan 200
Sw1(config-vlan)#private-vlan community
Creating isolated VLAN
Sw1(config)# vlan 300
Sw1(config-vlan)#private-vlan isolated
Creating primary VLAN and joining it with primary VLAN
Sw1(config)# vlan 500
Sw1(config-vlan)#private-vlan primary
Sw1(config-vlan)#private-vlan association 100,200,300
To proceed to next step, we must understand about different types of ports
There are mainly two types of port in Private VLAN - Promiscuous port and Host port. Host port is further divides into two types - Isolated port and Community port.
- Promiscuous port : This port can communicate with anything connected to primary or secondary VLANs. Usually, router, firewall etc. are connect to this port
- Isolated port: This port connect to hosts within the isolated VLAN. It can only communicate with the promiscuous port
- Community port : This port connect to hosts within the community VLAN. It can communicate with promiscuous port and other ports in the same community VLAN
Now, lets assign these different types of port to different VLANs we created. Remember, every ports except Promiscuous port are host port. So the VLAN which we assign these ports determines whether it is isolated port or community port.
SW1(config)#int range e0/1 - 2
SW1(config-if-range)#switchport
SW1(config-if-range)#switchport mode private-vlan host
SW1(config-if-range)#switchport private-vlan host-association 500 300
SW1(config)#int range e1/0 - 1
SW1(config-if-range)#switchport
SW1(config-if-range)#switchport private-vlan host-association 500 100
SW1(config)#int range e1/2 - 3
SW1(config-if-range)#switchport
SW1(config-if-range)#switchport private-vlan host-association 500 200
SW1(config)#int e0/0
SW1(config-if)#switchport
SW1(config-if)#switchport mode private-vlan promiscuous
SW1(config-if)#switchport private-vlan mapping 500 100,200,300
Basic Network Configuration of Linux System
Main configuration files
- /etc/hostname : contains name of host machine ; give the hostname in this file to permanently change the hostname. Otherwise, use "hostname" command to change the hostname temporarily
- /etc/hosts : Contains Name to IP mapping in the local system
- /etc/resolv.conf : Contains address of DNS servers
- /etc/nsswitch.conf : Determines order in which name resolution take place in system. We can change the order in this file to configure system to check first DNS then host file etc.
Redhat Network Files
- /etc/sysconfig/networks-scripts/ifcfg-eth0 : IP address information stored here
- /etc/sysconfig/network : This file contains the hostname; but this is a non standard way, Ubuntu/Debain is using the correct way
Debian/Ubuntu Network files
- /etc/network/interfaces
Commands to configure network
- Ifconfig : dipsplay and configure network interfaces
#ifconfig eth0 192.168.1.22 (set the IP of Ethernet 0 interface to 192.168.1.22)
#ifconfig eth0 netmask 255.255.255.0 (set the subnet mask)
#ifconfig eth0 hw ether 00:00:00:00:00:11 (To change the MAC address of eth0 interface)
#route add default gw 192.168.1.1 (To change the default gateway)
- Ifup : configure and activate network interface based on config files
#ifup eth0
- Ifdown- disable configured network interfaces
#ifdown eth0
Wednesday, December 21, 2011
Commonly Using Port Numbers
| Port | TCP | UDP | Description |
| 20 | x | FTP-Data | |
| 21 | x | FTP (login access) | |
| 22 | x | x | SSH |
| 23 | x | Telent | |
| 25 | x | SMTP (Mail, MTA) | |
| 49 | x | TACACS+ | |
| 53 | x | x | DNS |
| 69 | x | TFTP | |
| 80 | x | x | HTTP (Web) |
| 110 | x | x | POP3 (email); generally uses TCP) |
| 119 | x | NNTP (Usenet News) | |
| 123 | x | NTP | |
| 139 | x | x | NetBIOS (Microsoft) |
| 143 | x | x | IMAP |
| 161 | x | x | SNMP (Network Monitor) |
| 179 | x | BGP | |
| 443 | x | x | HTTPS |
| 465 | x | SMTPS (Secure Mail over SSL) | |
| 993 | x | x | IMAP (Secure IMAP over SSL) |
| 995 | x | x | POP3S (Secure POP3 over SSL) |
| 1645,1812 | x | RADIUS Authentication | |
| 1646,1813 | x | RADIUS Accounting |
Sunday, December 18, 2011
Installing Active directory in Windows Server 2008
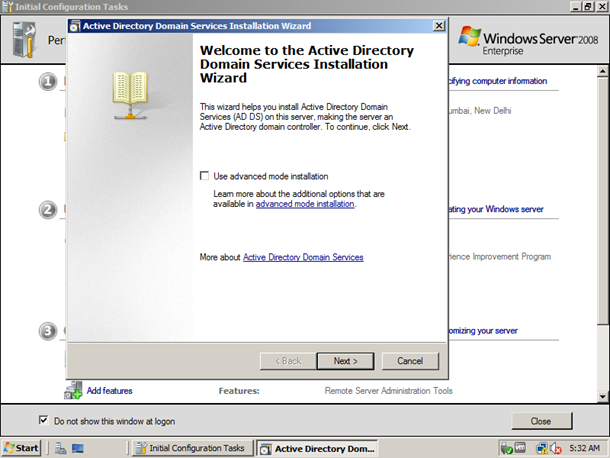
Before starting installation process, make sure that the IP address computer name are correct. Now use server manager to add rolls or type “oobe” in the command prompt. Now the following window will appear:
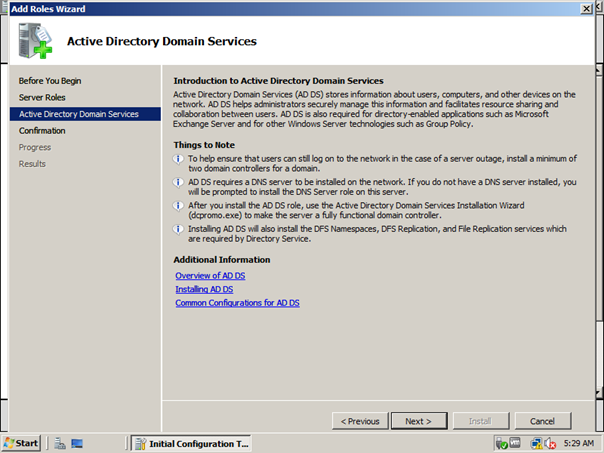
Press add roles and now press next
Select the Active directory Domain Services check box and press next . This tells the server we want to install active directory
Press next
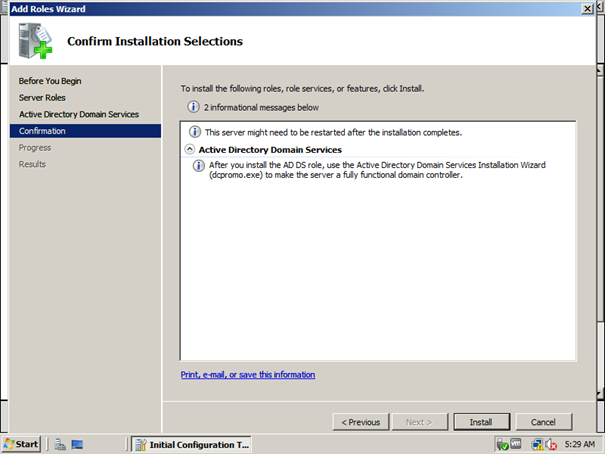
press next
press install
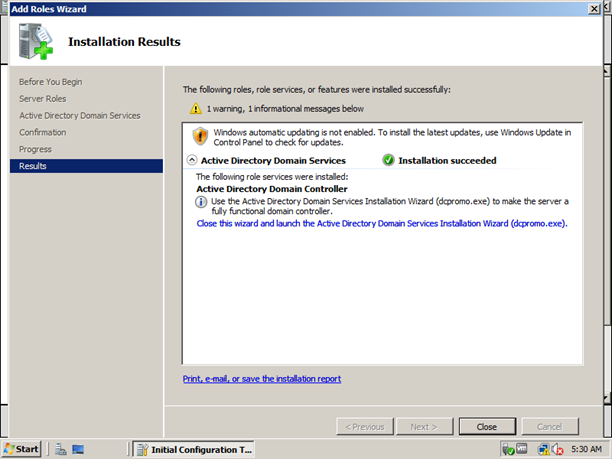
now we may close this wizard, if we close we need to type “dcpromo” on the command prompt and continue installation. Otherwise, press the link in the window highlighted by blue
Note : all the above steps can be done just typing “dcpromo” in the command prompt.
We are using normal mode. So press next. Advanced mode installation can be used to install read only domain controller
Press next if we are not using NT4 computers
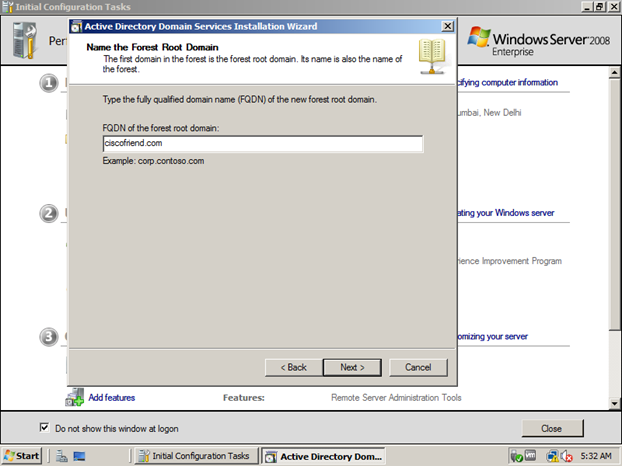
Now Select “Create a new domain in a new forest” because we are creating new domain. If we have existing domain and we want to add additional domain controller, add child domain etc. we must use the other option
Enter the domain name for our new domain
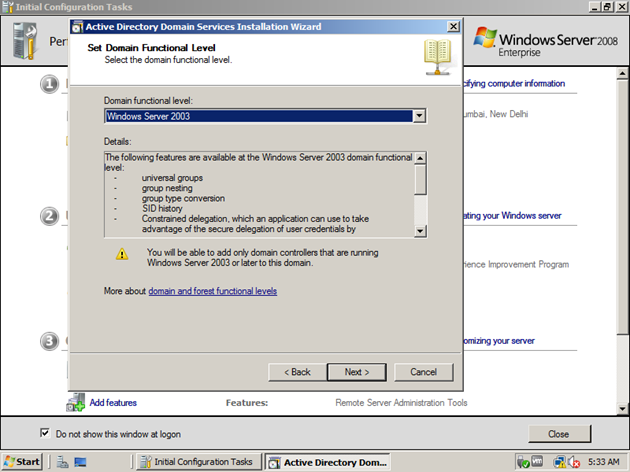
Enter the forest functional level. If forest functional level /domain functional level is higher, more features will be enabled. I will explain about forest and domain functional level in another post.
Enter the domain functional level. As above, higher is better
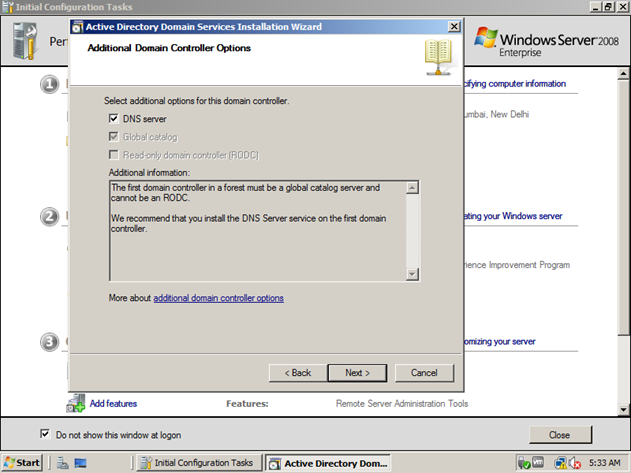
Select DNS because we don’t have another DNS server. If we have another one, we can use that one.
Note: If static IP not given already, it will give the warning. We can also give the IP address here. if error occurs again, that means you didn’t given IPv6 address. To solve this problem, either give IPv6 address or disable IPv6 addressing by removing check mark in the configuration window of Network card
Press yes and next
Press next if we don’t want to change the location of active directory files. NTDS is the active directory database
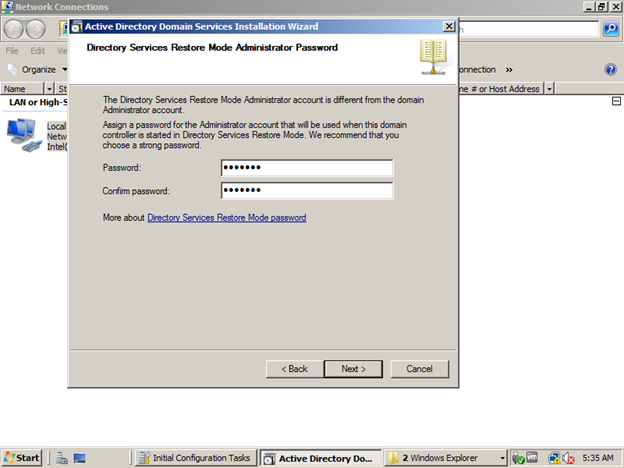
Give the password to restore active directory if any problem occurs and press next
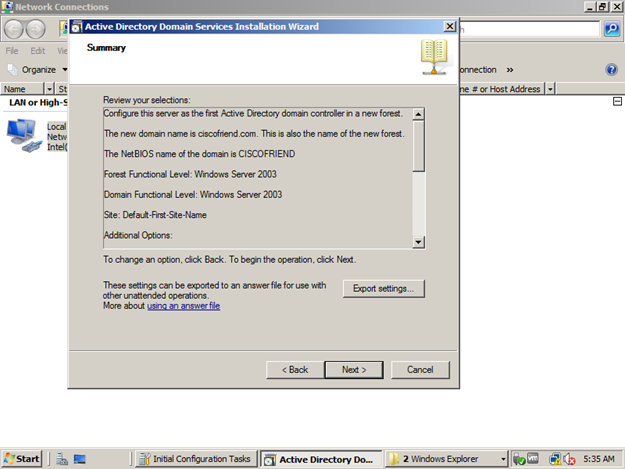
This window gives the summary of the answer we already given. If we want, we can press the export button to save the answer file for future installation or command line installation
Now active directory installation starts and tick the check box reboot on completion
After that reboot, we can see the role is installed in server manager. Also check the computer properties for details
Thursday, December 8, 2011
Upgrading Windows Server 2003 to Windows Server 2008
Before joining/upgrading the Windows Server 2003 to Windows server 2008 domain, we need to upgrade the schema. To check the scheme is in old version or not, do the following:
Open windows registry by type regedit on the command prompt and go to
Hkey_local_machine > system > current control set > services > ntds> schema version
now check the version :
- 31 means old
- 44 means new (windows server 2008)
If it is 31, it means we need to upgrade the schema. To upgrade the schema and make it ready for windows server 2008, do the following:
In the Windows Server 2008 DVD, go to sources > adprep directory and do the following commands
d:\souces\adprep> adprep /forestprep
d:\souces\adprep> adprep /domainprep /gpprep
notes:
- here My dvd drive is D:
- /gpprep : used to changes permissions on group policy objects
Now, we can join the server to Windows Server 2008 domain or if it is already a domain controller, we can upgrade it to Windows Server 2008
Tuesday, December 6, 2011
HTTP installation of RHEL6/CentOS/SL-6
On Server
#yum install httpd
Note: if you don’t know how to setup yum you can see this post
- Mount the DVD (which is also specified in the above post) and copy the content to /var/www/html/cdrom
For example, if DVD is mounted to /cdrom directory, then
#cp –vrf /cdrom /var/www/html/
Note: alternatively, we can mount the DVD directly to the web accessible, /var/www/html/ path
- Now, start the http service
#service httpd start
- Check the setting using the web browser with server’s IP. If server IP is 192.168.1.10 then use http://192.168.1.10/cdrom
Note: if firewall is on, turn off firewall or add exception to port 80
On the installation system
- Download boot.iso from redhat.
Note: boot.iso not ship with DVD now. So we need to download it from redhat site. Alternatively we can use CentOS netinstall.iso, both are same
http://mirrors.hns.net.in/centos/6.0/isos/x86_64/CentOS-6.0-x86_64-netinstall.iso
http://mirrors.hns.net.in/centos/6.0/isos/i386/CentOS-6.0-i386-netinstall.iso
- Write the the image to a CD and put it in the CD-ROM drive. Alternatively, we can use USB key. It is explained here.
- Reboot the system and supply the following boot string at the end of current line without quotes by pressing tab
'linux repo=http://192.168.1.10/cdrom ip=192.168.1.20 netmask=255.255.255.0 gateway=192.168.1.1 dns=192.168.1.1'
Note: if more than one DNS server is available specify it using comma. DNS server address is optional. Here IP is the address of the current system
Monday, December 5, 2011
Making CD/DVD as yum repository
1. Mount the CD/DVD to a folder
# mount -t iso9660 -o ro /dev/cdrom /cdrom
2. Create a repository file for that folder in /etc/yum.repos.d/
# nano /etc/yum.repos.d/cdrom.repo
Now add the following content to the file and save the file
[cdrom]
name=CD repo
baseurl=file:///cdrom
gpgcheck=0
Now we can install software using the yum command
Saturday, December 3, 2011
Disable login of all users except root
sudo touch /etc/nologin
Note: Now, only root can login to the system. Login as root and delete that file to allow other users to login
rm /etc/nologin
Tuesday, November 29, 2011
Monitoring Internet Connection using IP SLA
Our company may have two connection to the internet through 2 ISPs. If we want to use one connection as primary and other as backup, we can use IP SLA to monitor the link. It detects the link failure even if the connection between modem and ISP fails. So it helps to switch over to the backup path automatically as soon as the primary path is down.
Step1 : Configuring SLA process
R1(config)#ip sla 1
R1(config-ip-sla)#icmp-echo 8.8.8.8
R1(config-ip-sla-echo)#frequency 5 (Means, every 5 second send icmp-echo packet to the ip 8.8.8.8. This can by any reliable IP on internet)
R1(config-ip-sla-echo)#exit
Step2: Scheduling SLA process
R1(config)#ip sla schedule 1 start-time now life forever (Means, start the sla process now and don’t end)
Note: we can check the process using the following command
R1#show ip sla statistics
Step3: Create a track object to track the change. It is used to inform the router about the current condition
R1(config)#track 10 rtr 1 reachability (this will inform the router if any reachability problem occurs. rtr is the old name of IP SLA)
R1(config-track)#exit
Step4: Create two static route two both ISPs with some tweaks
R1(config)#ip route 0.0.0.0 0.0.0.0 fastEthernet 0/0 track 10
R1(config)#ip route 0.0.0.0 0.0.0.0 fastEthernet 0/1 2
Now router will select ISP1 as primary path because of administrative distance is lower. If the link to ISP1 is down, then router automatically switch the connection to ISP2
Monday, November 28, 2011
ASA static/Default Routing configuration

Syntax of static route configuration is :
Route <interface-name> <ip address> <netmask> <gateway ip> [distance]
Objects:
- Configure static routing to inside interface
ASA1(config)#route inside 172.30.10.0 255.255.255.0 172.30.30.2 1
ASA1(config)#route inside 172.30.20.0 255.255.255.0 172.30.30.2 1
- Configure default route to internet
ASA1(config)#route outside 0.0.0.0 0.0.0.0 192.168.1.2Note: we can use the command “route outside 0 0 192.168.1.2” for default route, both are same.
Saturday, November 26, 2011
Network Time Protocol (NTP) configuration
If you want to synchronize with NTP server just now, then execute the following command:
$ sudo ntpdate 1.in.pool.ntp.org
Here 1.in.pool.ntp.org is the NTP server we are synchronizing with. You can find closer NTP server to your country from www.pool.ntp.org
NTP automatic synchronization through service
$ sudo apt-get install ntp
$ sudo service ntp start
If you want to synchronize with more closer NTP servers, then edit ntp.conf file by replacing the existing NTP servers with closer servers.
$ sudo nano /etc/ntp.conf
now change ntp servers if you want and save the file and restart the service
$ sudo service ntp restart
NOTE: if you are running other distributions than Ubuntu, then login as root and run the command without “sudo” in front of it
Friday, November 25, 2011
automatic login Ubuntu 11.10
sudo nano /etc/lightdm/lightdm.conf
now under [SeatDefaults], add the following
autologin-user=binoy
Note: here username is “binoy” . change it to your user name
Wednesday, November 23, 2011
Linux/Unix file system Hierarchy
| / | root directory |
| /bin | command binaries |
| /boot | boot loader |
| /dev | devices |
| /etc | configuration files |
| /home | user home directories (MacOSX uses ‘USERS’ directory to store home directories of users) |
| /lib | library files for executables |
| /proc | virtual file system (information about current running system) |
| /root | root user home directory |
| /sbin | system binaries (binaries that should run by system not users) |
| /tmp | temporary file storage |
| /usr | user binaries , often read only; (install by user like open office) |
| /var | variable files, log, mail |
| /media | mount place for removable media |
| /mnt | legacy location for removable media |
Sunday, November 6, 2011
createrepo rpm installation problem – solution
Error:
[root@server1 Packages]# rpm -ivh createrepo-0.9.8-4.el6.noarch.rpm
warning: createrepo-0.9.8-4.el6.noarch.rpm: Header V3 RSA/SHA256 Signature, key ID fd431d51: NOKEY
error: Failed dependencies:
deltarpm is needed by createrepo-0.9.8-4.el6.noarch
python-deltarpm is needed by createrepo-0.9.8-4.el6.noarch
Solution:
rpm -ivh createrepo-0.9.8-4.el6.noarch.rpm deltarpm* python-deltarpm*
Friday, November 4, 2011
Installing GNS3 on CentOS 6.x/RHEL 6.x/Fedora 15
- Login as root then do the following steps:
yum install python python-devel xorg-x11-proto-devel libXext-devel gcc-c++ libXrender* - Download and install Qt
#wget http://get.qt.nokia.com/qt/source/qt-everywhere-opensource-src-4.7.4.tar.gz
#tar -xzf qt-everywhere-opensource-src-4.7.4.tar.gz
#cd qt-everywhere-opensource-src-4.7.4
#./configure -nomake examples -nomake demos -qt-gif -no-exceptions -debug -qt3support
#gmake
#gmake install
#PATH=/usr/local/Trolltech/Qt-4.7.4/bin:$PATH
#export PATH - Download and install sip
#wget http://www.riverbankcomputing.co.uk/static/Downloads/sip4/sip-4.13.tar.gz
#tar -xvf sip-4.13.tar.gz
#cd sip-4.13.tar
#python configure.py
#make
#make install - Download and install PyQt
#wget http://ftp.pardus.org.tr/pub/source/2009/PyQt-x11-gpl-4.8.4.tar.gz
#tar xvf PyQt-x11-gpl-4.8.4.tar.gz
#cd PyQt-x11-gpl-4.8.4
#python configure.py -q /usr/local/Trolltech/Qt-4.7.4/bin/qmake
#make
#make install - Download GNS3
#wget http://downloads.sourceforge.net/project/gns-3/GNS3/0.7.4/GNS3-0.7.4-src.tar.gz
#tar -xvf GNS3*.tar.gz && rm GNS3*.tar.gz
#cd GNS3-0.7.4-src
#mkdir Dynamips IOS Project Cache Temp - Download Dynamips depending up on OS (64-bit/32-bit)
#cd dynamips
#wget http://downloads.sourceforge.net/gns-3/dynamips-0.2.8-RC2-amd64.bin?download (for 64-bit OS)
#wget http://downloads.sourceforge.net/gns-3/dynamips-0.2.8-RC3-community-x86.bin?download (for 32-bit OS)
#chmod +x dynamips-0.2.8-RC2-amd64.bin (if we use 32-bit version, use the name of that file) - Creating Quick launch with gns3 icon
#wget http://www.noahbeach.com/wp-content/uploads/2011/08/gns3.png
Now right click on the panel and select add to panel > custom launcher > select the gns3 location and press on the icon button to locate the icon just downloaded. ok
Now if we press that icon in the panel, gns3 will run...!!!
Saturday, October 29, 2011
Preparing a bootable RHEL6 Bootable Pen drive
- Go to images sub directory of RHEL DVD
- If the location of the pen drive is /dev/sdd, write the image to pen drive using the following command:
#dd if=efidisk.img of=/dev/sdd
Note: This command will overwrite all existing data on the drive
Monday, October 24, 2011
Configuring router for SDM

SDM configuration steps:
- Create user accounts
- Enable http and/or https server
- Configure http to use local user database
R1(config)#username binoy privilege 15 secret ciscoNow download SDM from www.cisco.com/go/sdm and install it in the computer (requires java runtime environment) and launch the SDM by giving IP address in SDM launcher
R1(config)#ip http server
R1(config)#ip http secure-server (allows encrypted access)
R1(config)#ip http authentication local
Wednesday, October 19, 2011
Cisco router password recovery process
- Connect to console port
- Use the power switch to power cycle the router.

- Issue the break sequence within 60 seconds of power up to put the router into ROMmon.
- Type “confreg 0x2142” at the rommon 1> prompt. (This changes the default configuration register and causes the router to bypass the startup configuration where the forgotten enable password is stored.The configuration register is usually set to 0x2102 or 0x102)
- Type no after each setup question, or press Ctrl-C to skip the initial setup procedure.
- Router> enable
- Router#copy start run
- Now, change the passwords and give no shutdown commands to interfaces
- R1(config)# config-register 0x2102 (To make the startup configuration effective while next booting)
Sunday, October 9, 2011
Administrative Distance of Routing protocols
| Connected interface | 0 |
| Static route | 1 |
| Enhanced Interior Gateway Routing Protocol (EIGRP) summary route | 5 |
| External Border Gateway Protocol (BGP) | 20 |
| Internal EIGRP | 90 |
| IGRP | 100 |
| OSPF | 110 |
| Intermediate System-to-Intermediate System (IS-IS) | 115 |
| Routing Information Protocol (RIP) | 120 |
| Exterior Gateway Protocol (EGP) | 140 |
| On Demand Routing (ODR) | 160 |
| External EIGRP | 170 |
| Internal BGP | 200 |
| unknown | 255 |
Wednesday, September 28, 2011
Installing and configuring SecureCRT for gns3
Secure CRT Installation
- Download secureCRT with crack from internet (There are plenty of places, use google to search “SecureCRT with crack downlaod”)
- Install secureCRT
- copy the crack to installation directory (eg: C:\Program Files\VanDyke Software\SecureCRT\)
- Run the crack as administrator (Right click the crack and in the menu select run as administrator)

- Enter anything in name and company field and press generate. Now, the serials and other information appears.
- Press the patch button to patch the secureCRT.exe file. That’s it. Now the secure CRT installed correctly.
GNS3 configuration of secure CRT
- Download and install GNS3, add IOS etc.
- Go to Edit > Preferences > General > Terminal settings tab > SecureCRT > Change preconfigured terminal commands to SecureCRT (64 bit or 32 bit depending upon the version installed) > Press “use” button > press ok

- Now add some routers (with IOS added) to work space and turn it on.
- Press the console button to see the tabbed windows for each router
Monday, February 7, 2011
Can’t authorize DHCP server (solution)
If you can’t authorize the DHCP server which is installed on a member server, login as enterprise administrator and try it.
how to login as enterprise administrator from member server
If you are simply login as administrator with password, it will be the administrator account in the member server. So use the fully qualified name to login as enterprise administrator like administrator@home.internal
Thursday, February 3, 2011
asterisk with GUI (Asterisknow)

Download Asterisknow form here :
32 bit version: http://www.asterisk.org/downloads/asterisknow/i386/asterisknow32.iso
64 bit version: http://www.asterisk.org/downloads/asterisknow/x86_64/asterisknow64.iso
Sunday, January 30, 2011
Find the installation date of an OS
systeminfo | find /i "install date"
“John the ripper”….. the ultimate password cracker for Linux/Unix

Installation & configuration:
- Download John the ripper from www.openwall.com
- Do the following as root:
# tar -xzvf john-1.7.6.tar.gz (to extract)
# cd john-1.7.6/src/
# make (to see the platforms and select our platform)
# make linux-x86-64
# cd ../run/
- Now John is ready to run
#./john -users:binoy /etc/shadow (we can give multiple users separated by comma)
we can see the password on screen. Also, password will be stored in john.pot
# cat john.pot (to see the password)
# ./john -show -users:binoy /etc/shadow (it will show full details of that account in /etc/shadow file as below)
binoy:abc123:15003:0:99999:7:::
Friday, January 28, 2011
Bluefish……A great free Linux/Windows Editor
* C/C++
* CSS
* CFML
* gettext PO
* HTML
* Java
* JavaScript
* JSP
* Perl
* PHP
* Python
* Ruby
* Shell
* SQL
* XML
and plenty more features.

Go to http://bluefish.openoffice.nl/ for more details and installation instructions